Enabling Redis Keyspace Notifications in AWS ElastiCache

Redis is a very popular in-memory data store because of its speed and versatility. One of its powerful features is ...
Read more
What is Veeam Kasten and How Does It Work?

As more companies are moving towards cloud adoption and using containers, keeping data safe and secure becomes a top priority. ...
Read more
Deploy IAC Without Code Using CloudFormation Infrastructure Composer

AWS CloudFormation Infrastructure Composer is a newly launched tool of CloudFormation Service that lets us design, configure, and deploy AWS ...
Read more
Secure Amazon RDS for MySQL and SQL Server with SSL/TLS

Encrypting traffic between your applications and databases is essential for safeguarding sensitive information. For Amazon RDS running MySQL or Microsoft ...
Read more
New Next-Level ECS Monitoring with CloudWatch
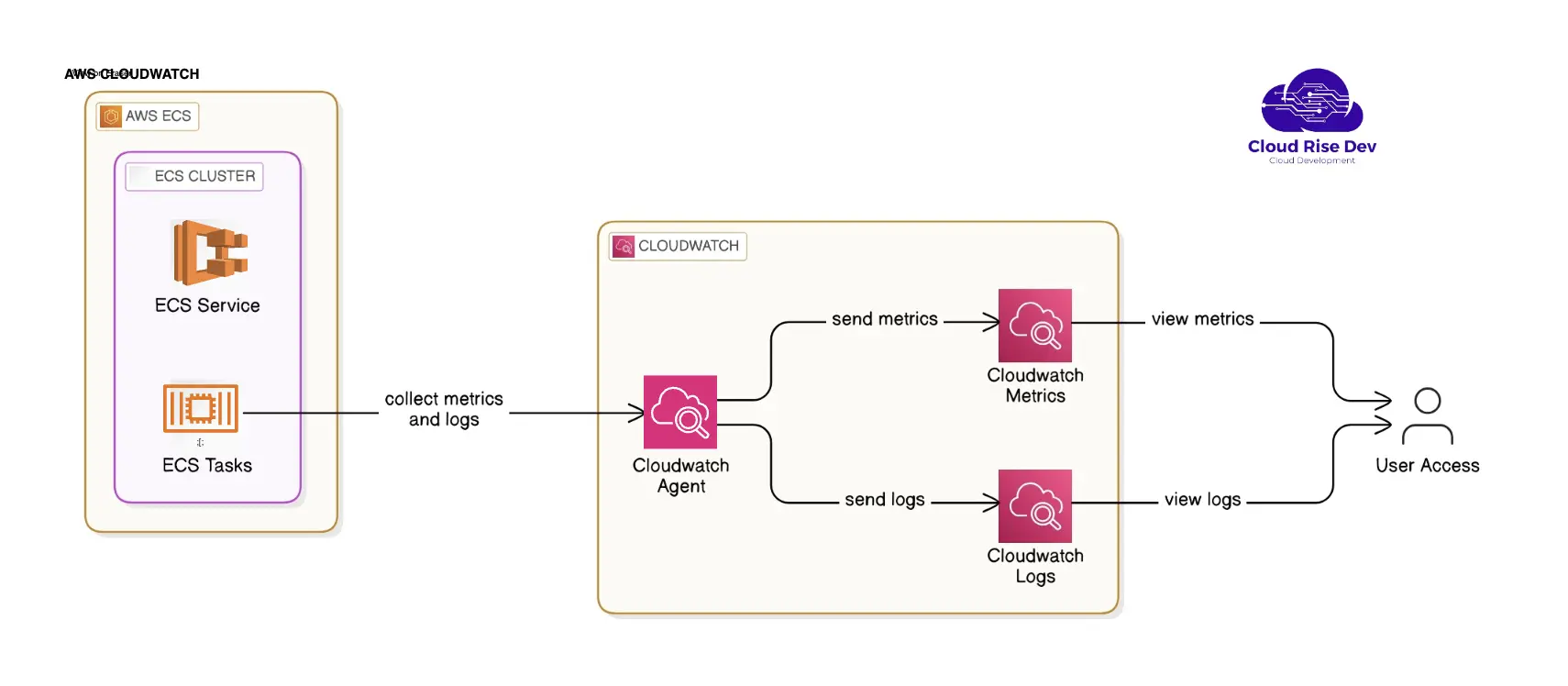
Modern container systems need regular monitoring to maintain system stability and maximum performance. The AWS team has added new features ...
Read more
5 New AWS Cost Optimization Features Launched

As we live in a world of cloud, cost optimization isn’t just good practice, it’s mandatory. If you’re on AWS, ...
Read more
How to Enable Cross-Account Access in AWS using IAM
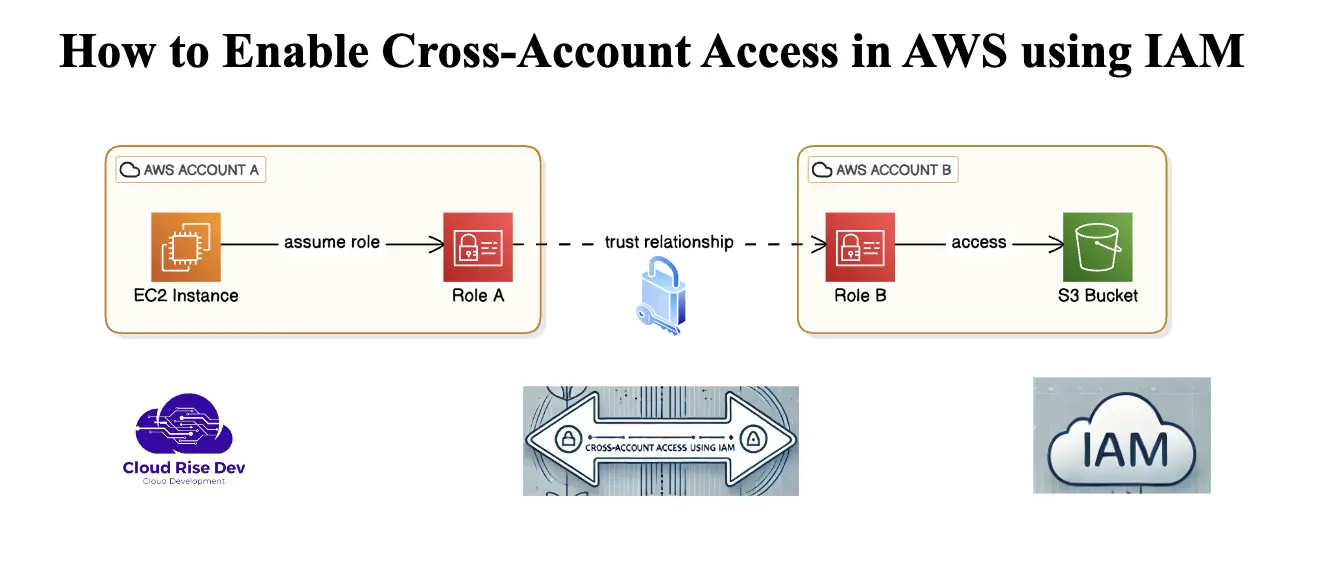
Step 1: Create a Role in the Target Account Navigate to the IAM Console Choose Trusted Entity Attach Policies Name ...
Read more
Increasing Security Investigations with Amazon Detective

What is Amazon Detective? Amazon Detective is optimized to generate and link large amounts of AWS logs. It offers an ...
Read more
Enhancing AI Workload Security with Amazon GuardDuty

Security of the AI workloads in today’s cloud environment is imperative. There is Amazon GuardDuty enables efficient and massive threat ...
Read more
Exploring OpenShift Virtualization on Red Hat OpenShift Service on AWS (ROSA)

As a result, mid-transformation enterprises have a need for cost efficient execution of both traditional “brown” workloads and newer “green” ...
Read more